Get started with McMaster Mail
Who can use it?
Staff, Faculty, Undergraduate and Graduate students.
How to get it
You must activate your MacID to use this service.
How much does it cost?
This service is free.
Service availability
24/7
Service Provider
McMaster Mail is powered by Microsoft (Office 365).
Information Box Group

McMaster Mail Licenses View license types
McMaster Mail is the email and calendaring service for many groups across the University. Learn more about what 365 integrations are available to each group.
McMaster Mail Licenses - View license types
McMaster Group |
License Description |
| Staff, Students, Faculty, Researcher | Suite of licensed applications with download capability |
| Contractor, MACID Email, NONMacSup, Upd Inst | Suite of licensed applications with web apps |
| Retiree (except professors emeritus) | Exchange Online (McMaster Mail email with web access only) |
| Professors Emeritus | Suite of licensed applications with download capability |
| Role-based accounts | Exchange Online (McMaster Mail email with web access only) |
| Person of Interest (POI) | Suite of licensed applications with web apps |

Accessing Email on Your Devices See recommendations
Recommendations on email clients for mobile devices and operating systems to ensure compatibility.
Accessing Email on Your Devices - See recommendations
Accessing McMaster Mail via web browser:
You can access McMaster Mail via most web browsers, including Internet Explorer, Chrome, Firefox, Edge, and Safari. The URL to access your email service is http://mail.mcmaster.ca/.
Recommended versions of Outlook on your PC or Mac:
- At minimum, Outlook 2016 is recommended.
- Upgrade to Microsoft 365 for the best functionality.
Recommendations for mobile devices:
| Device | Recommendation |
| Android | |
| Apple iOS |
|
| Apple Mac OS X |
|

McMaster Mail Benefits Learn More
Learn more about benefits and features of McMaster Mail.
Benefits
- Reliable integration with mobile devices
- Enhanced security
- Hosting in a Canadian data centre
- Document sharing capabilities
- Increase in file attachment size (150MB)
The Office 365 online tool will provide an advanced integration experience for anyone using collaborative tools such as Teams and OneDrive.
Setup Instructions
Instructions to add McMaster Mail to your mobile device or laptop are listed below.
If you have any questions, or are unable to resolve your issue, support can be received via the Service Desk
Information Box Group
Mobile iOS Set up Mobile iOS
Set up McMaster Mail for Mobile iOS
Set up Mobile iOS
Mobile IOS
- Download Outlook for iOS from the iOS App Store and then open it.
- If it’s your first time using Outlook for iOS, enter your full McMaster email address, then tap Add Account. If you already use Outlook for iOS for a different email, open the Menu > tap Settings > Add Account > Add Email Account.
- Enter your email account password and tap Sign In
- When prompted, authenticate your sign-in using your preferred method of multi-factor authentication.
Android Set up Android
Set up McMaster Mail for Android
Set up Android
Android
- Install the Outlook for Android app from the Google Play Store and then open it.
- Tap Get Started if this is your first time. You may see a prompt to connect a google account, just follow the steps on screen or press skip if you do not want your personal accounts connected.
- If you already use Outlook for Android, to add another email account open the Menu > click Settings > click Add Account > click Add Email Account.
- Enter your full McMaster email address (your MacID@mcmaster.ca), then tap Continue
- Enter your email account password and tap Sign In
- When prompted, authenticate your sign-in using your preferred method of multi-factor authentication.
MAC iOS Set up MACiOS
Set up McMaster Mail for MAC iOS
Set up MACiOS
MAC iOS
- Open Outlook.
- Type in your email address and password.
- Select Add Account and type in your full McMaster email address (your MacID@mcmaster.ca) and password.
- Select Done.
- To add another account, select Tools > Accounts. Then select the plus (+) sign > New Account.
Through Web Browser Set up through Web Browser
Set up McMaster Mail through your Web Browser
Set up through Web Browser
Through Web Browser
- Open a new tab in Google Chrome and type in Office.com.
- Sign into Office.com by entering your full McMaster email address (your MacID@mcmaster.ca) and password.
- Once signed in, select ‘Outlook’.
Windows/PC Set up Windows/PC
Set up McMaster Mail for Windows/PC
Set up Windows/PC
Windows/PC
- Open Outlook and select File > Add Account. If you haven’t launched Outlook before, you’ll see a welcome screen.
- Enter your email address (your MacID@mcmaster.ca) and select Connect. If your screen looks different- enter your name, email address, and password. Then select Next.
- If prompted, enter your password and select OK.
- Select Finish.
Set up through the Gmail App
- On your phone or tablet, open the Gmail app.
- In the top right, tap your profile picture.
- Tap Add another account.
- Tap Outlook to add your McMaster Email.
- Follow the steps on the screen to add your account, signing into outlook using your usual McMaster email and password.
Training and How-To’s
Use the information below to help you effectively manage your email and data. Are you a graduating student, be sure to download and/or move your data advance of your term end date.
If you have any questions, or are unable to resolve your issue, support can be received via the Service Desk
How To's
Manage Incoming Mail Effectively - View Steps to Manage Email
1. SPAM EMAILS
What To Do:
If you receive mail from a sender you recognize and you cannot unsubscribe, you can BLOCK them and move the mail to your JUNK folder
You are protected against spam under Canada’s anti-spam legislation (CASL). Learn about the legislation as well as how to protect yourself from spam and how to report it when necessary.
If you have not given permission to receive unwanted mail from a sender, you can also report them to the Canadian Radio-television and Telecommunications Commission.
2. PHISHING EMAILS
Phishing is a type of online attack in which an attacker — using both technological and psychological tactics — sends one or more individuals an unsolicited email, social media post, or instant message designed to trick the recipient into revealing sensitive information or downloading malware.
Phishing attacks can be generic or customized and can target both individuals and entire organizations. Attacks that target a specific individual or organization are commonly referred to as spear phishing attacks.
The main goal of a phishing attack is to get the individual to do something that compromises the security of their system and/or potentially their organization. To stop attackers from achieving this, when you receive a suspicious email:
- Be Careful of opening email attachments from unsolicited senders. Email attachments can contain malware.
- Be Careful of links. Fake websites or pages can install malware. Hover our mouse over links to see the destination URL.
- Be Careful of entering usernames, passwords, or other sensitive information on websites. Hackers can create fake yet identical login pages. If possible, navigate to the website manually.
- DO NOT reply to phishing emails with confidential information such as login credentials. No McMaster email address will ask for your credentials.
Phishing messages can range from very basic to highly sophisticated. Common “red flags” or indicators include:
- The suspicious sender or reply-to address: always treat messages from unknown or unfamiliar senders or accounts with extra caution.
- Unexpected message: messages from recognized senders that are unrelated to normal communications or job responsibilities can signal an account has been compromised or is fake.
- Suspicious attachment: messages with unexpected or unusual attachments can contain malware.
- Suspicious link: messages that encourage recipients to click and follow embedded hyperlinks may point to websites unrelated to the message and under the control of the attackers.
- Poor spelling: spelling and grammar errors may indicate a phishing attack since legitimate organizations typically avoid these mistakes in their communications.
What To Do:
If you think you have been phished or hacked, don’t be embarrassed. The best thing to do is report to the UTS Service Desk.
All suspicious messages must be reported to is-spam@mcmaster.ca and the message should be deleted from your inbox and your deleted folder. Reporting phishing attempts and suspicious messages helps keep the McMaster community safer.
Then, delete or move the emails to JUNK.
Click here for more information and training regarding phishing and reporting.
3. HARASSMENT EMAILS
McMaster Community Members who have experienced unwelcome comments or conduct by another person are encouraged, although not obliged, to make it known to the other person that their behaviour is unwelcome.
What To Do:
In situations where it is believed that addressing the other person could lead to an escalation of the comment or conduct or safety risks, this approach is not recommended. If the problem is not resolved, or if you feel you cannot respond directly to the other person, notify an appropriate Supervisor, or contact HR (staff) or Campus Police (staff and students).
Access the Harassment and Discrimination Policy.
Use a RULE to move the emails to Junk or keep them in a separate folder for investigation. Rules can also help filter out specific words/names that repeatedly come from different or hidden email addresses.
4. CREATING RULES
Rules allow you to move, flag, and respond to email messages automatically. You can also use rules to play sounds, move messages to folders, or display new item alerts.
The easiest and most common rule to create is one that allows you to move an item from a certain sender or with certain words in the subject line to another folder. You can create this rule directly from a message you’ve already received.
5. BLOCK SENDERS OR MARK EMAIL AS JUNK (AND OTHER OPTIONS)
6. HOW TO MANAGE JUNK MAIL
No one likes spam or junk email. The Outlook Junk Email Filter doesn’t stop the delivery of junk email messages, but does the next best thing—it moves suspected spam to the Junk Email folder.
7. CHANGE HOW YOUR MAIL GETS ORGANIZED IN THE FOCUSED AND OTHER MAIL TABS
8. MORE OUTLOOK (EMAIL) TRAINING
Training

Upcoming training sessions Register here
UTS and Microsoft will host a number of support sessions to help you make the most of Student Mail and other 365 applications.

Microsoft Outlook tutorials View video tutorials
Discover tutorials, videos, training, and more, all provided by Microsoft.
LinkedIn Learning View video tutorials
A list of LinkedIn Learning courses to help you manage your appointments, share calendars, work with contacts, and stay on task with Outlook 2016 and Microsoft 365.

Accessibility Webinars Sessions
Learn about accessibility features of Microsoft 365, such as Word and PowerPoint.
Support

Support for Microsoft365 Applications Get Support
Get detailed support and training on all MS365 applications.
- Home
- McMaster Mail
Email Quarantine
Email Quarantine
Email Quarantine prevents email messages that have a high probability of being spam, phishing, or malware from going into your mailbox.
You will receive an email notification from Microsoft once a day if any emails have been quarantined that day. Emails are held in your quarantine for 30 days.
It is recommended that you check your email quarantine page regularly to review any messages that have been quarantined.
Information Box Group
Managing your email quarantine Learn how to manage your quarantine
See FAQs, best practices and tips and tricks on how to manage your email quarantine on the Discover and Learn Website:
Why email quarantine? Learn more about email phishing
This tool safeguards you and the McMaster community by preventing potentially harmful messages from reaching your inbox, where accidental clicks or responses could expose you to phishing or malware attacks.
McMaster Mail FAQ
If you have any questions, or are unable to resolve your issue, support can be received via the Service Desk
General FAQs
If you are using the Outlook email client on your device, you will be able to access your email using your MACID@mcmaster.ca and password. To access your new email service, the URL is mail.mcmaster.ca.
To login via Outlook client, enter your MACID@mcmaster.ca and password:
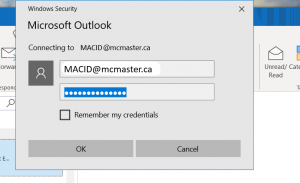
If you cannot log into mail.mcmaster.ca please contact the UTS Service Desk:
- Log into servicedesk.mcmaster.ca
- Click on the Email Migration Issue form
- Please fill out all the details so support will know how to contact you and research your issue before contacting you.
McMaster will support Microsoft Outlook and Apple Mail.
Students email accounts will expire January 31 after your convocation. Contact the McMaster Alumni Association for email forwarding.
At minimum, Outlook 2016 is recommended. Upgrade to Microsoft 365 for the best functionality.
- Outlook will turn on a “Focused Inbox” that separates incoming messages into two tabs—Focused and Other. The most important messages will filter into the Focused tab. For information on this feature (and how to disable it), please see this Microsoft article.
- Reliable integration with mobile devices
- Enhanced security
- Hosting in a Canadian data centre
- Enhanced collaborative tool functionality
- Document sharing capabilities
- Integration with Teams
To recover deleted emails in McMaster Mail, follow these steps.
If your emails to a specific recipient keep bouncing back with an email address that looks like this:
IMCEAEX-_O=MCMASTER+20UNIVERSITY_OU=xxxx_cn=xxx_cn=xxx@CANPRD01.PROD.OUTLOOK.COM
…it might be caused by a cached email address. Caching is the process of Outlook “remembering” information for fast retrieval. Follow these instructions to fix bounce back emails that are a result of previously cached email addresses.
1. SPAM EMAILS
What To Do:
If you receive mail from a sender you recognize and you cannot unsubscribe, you can BLOCK them and move the mail to your JUNK folder
You are protected against spam under Canada’s anti-spam legislation (CASL). Learn about the legislation as well as how to protect yourself from spam and how to report it when necessary.
If you have not given permission to receive unwanted mail from a sender, you can also report them to the Canadian Radio-television and Telecommunications Commission.
2. PHISHING EMAILS
Phishing is a type of online attack in which an attacker — using both technological and psychological tactics — sends one or more individuals an unsolicited email, social media post, or instant message designed to trick the recipient into revealing sensitive information or downloading malware.
Phishing attacks can be generic or customized and can target both individuals and entire organizations. Attacks that target a specific individual or organization are commonly referred to as spear phishing attacks.
The main goal of a phishing attack is to get the individual to do something that compromises the security of their system and/or potentially their organization. To stop attackers from achieving this, when you receive a suspicious email:
- Be Careful of opening email attachments from unsolicited senders. Email attachments can contain malware.
- Be Careful of links. Fake websites or pages can install malware. Hover our mouse over links to see the destination URL.
- Be Careful of entering usernames, passwords, or other sensitive information on websites. Hackers can create fake yet identical login pages. If possible, navigate to the website manually.
- DO NOT reply to phishing emails with confidential information such as login credentials. No McMaster email address will ask for your credentials.
Phishing messages can range from very basic to highly sophisticated. Common “red flags” or indicators include:
- The suspicious sender or reply-to address: always treat messages from unknown or unfamiliar senders or accounts with extra caution.
- Unexpected message: messages from recognized senders that are unrelated to normal communications or job responsibilities can signal an account has been compromised or is fake.
- Suspicious attachment: messages with unexpected or unusual attachments can contain malware.
- Suspicious link: messages that encourage recipients to click and follow embedded hyperlinks may point to websites unrelated to the message and under the control of the attackers.
- Poor spelling: spelling and grammar errors may indicate a phishing attack since legitimate organizations typically avoid these mistakes in their communications.
What To Do:
If you think you have been phished or hacked, don’t be embarrassed. The best thing to do is report to the UTS Service Desk.
All suspicious messages must be reported to is-spam@mcmaster.ca and the message should be deleted from your inbox and your deleted folder. Reporting phishing attempts and suspicious messages helps keep the McMaster community safer.
Then, delete or move the emails to JUNK.
Accessing the phishing homepage and take the training course.
3. HARASSMENT EMAILS
McMaster Community Members who have experienced unwelcome comments or conduct by another person are encouraged, although not obliged, to make it known to the other person that their behaviour is unwelcome.
What To Do:
In situations where it is believed that addressing the other person could lead to an escalation of the comment or conduct or safety risks, this approach is not recommended. If the problem is not resolved, or if you feel you cannot respond directly to the other person, notify an appropriate Supervisor, or contact HR (staff) or Campus Police (staff and students).
Access the harassment and discrimination policy.
Use a RULE to move the emails to Junk or keep them in a separate folder for investigation. Rules can also help filter out specific words/names that repeatedly come from different or hidden email addresses.
4. CREATING RULES
Rules allow you to move, flag, and respond to email messages automatically. You can also use rules to play sounds, move messages to folders, or display new item alerts.
The easiest and most common rule to create is one that allows you to move an item from a certain sender or with certain words in the subject line to another folder. You can create this rule directly from a message you’ve already received.
5. BLOCK SENDERS OR MARK EMAIL AS JUNK (AND OTHER OPTIONS)
6. HOW TO MANAGE JUNK MAIL
No one likes spam or junk email. The Outlook Junk Email Filter doesn’t stop the delivery of junk email messages, but does the next best thing—it moves suspected spam to the Junk Email folder.
7. CHANGE HOW YOUR MAIL GETS ORGANIZED IN THE FOCUSED AND OTHER MAIL TABS
8. MORE OUTLOOK (EMAIL) TRAINING
The cloud is just as secure as on-premise. In fact, the cloud solution comes with features that will enable us to make it even more secure such as conditional access, spam controls, and multi-factor authentication. Moving forward, McMaster University will look to take advantage of these advanced features.
A Focused Inbox separates your inbox into two tabs – Focused and Other. Your most important email messages are on the Focused tab while the rest remain easily accessible – but out of the way in the Other tab.
Want to turn on your Focused Inbox ‘on’ or ‘off’?
Access the step-by-step focused Inbox guidelines.
- Find the photo that you would like to use on your computer or OneDrive. The photo must be smaller than 4 MB and can be a .png, jpg, or .gif file.
- Sign into Microsoft 365 at office.com with your work or school account.
- Select the circle in the upper right-hand corner of the page that shows your initials or an icon of a person
![]()
- In the ‘My accounts’ pane, select the circle that shows your initials or an icon of a person. Change your photo in the pop-up that appears.
There are a number of ways that McMaster Mail (powered by Microsoft 365) works with Microsoft Teams for an enhanced calendaring experience. Check out the videos below to see the new meeting and scheduling functionality available to users after they migrate.
Please visit Microsoft 365 Storage Limits for details on OneDrive storage.
Guidance for bulk mailers in response to changes by Google and Yahoo
Beginning in February, Google and Yahoo are implementing new requirements for bulk email senders to reduce spam for Gmail users. Other email service providers, such as Microsoft, may soon follow suit.
If you or your team use an ‘@mcmaster.ca’ email address to send mass email to EXTERNAL non-McMaster email accounts (ex. Gmail or Yahoo) via a third-party service (ex. Mail Chimp, Constant Contact), those emails sent to recipients with Gmail and Yahoo accounts may be blocked starting in February 2024.
To avoid potential impact, it is recommended that you follow these steps:
- Test delivery to Gmail and Yahoo – add a ‘test’ Gmail and Yahoo account in your mass mailing distribution list so you can check if your emails are being delivered to these accounts.
- List hygiene – Clean up your mass mailing list by removing any inactive Gmail accounts that should no longer be there. This may resolve the issue.
- Easy unsubscribe – Ensure that users can unsubscribe from commercial or promotional emails in one click and process requests within two days. Most third-party bulk senders should already have this measure in place. For further guidance, review CASL guidance on email consent
- Reduce spam reporting – If more than 0.3% of Gmail recipients mark your emails as spam, your emails will be blocked by Google accounts. Follow email best practices, such as having a clear subject line, to avoid being marked as spam.
- Authenticate the account/service you use to send bulk email – This adds a layer of security and verifies your identity as a ‘legitimate sender.’ Learn how to authenticate your account below.
You are only required to take action at this time if you send bulk email using an ‘@mcmaster.ca’ account via third party services (ex. Mail Chimp) to external, non-McMaster recipients. Otherwise, NO ACTION is required.
If you have any questions or concerns, please contact the UTS service desk.
Email Authentication: What, Why, and How
Email authentication is a way of verifying that an email sender is who they claim to be. It helps prevent spam, phishing, and spoofing, which are common techniques used by cybercriminals to trick recipients into opening malicious emails or revealing sensitive information.
Email authentication is especially important for bulk email senders, who send large volumes of emails to internal or external recipients via a third-party service such as Mail Chimp or Constant Contact.
At McMaster University, there are two main methods to authenticate a third-party bulk mailing account:
DKIM is a technical standard that authenticates you as a legitimate McMaster sender. This option will allow you to use your @mcmaster.ca email address as the sender of your bulk emails.
To do this, you will need to follow these steps:
- Generate your DKIM record from your email account or service. Your third-party service provider (ex. Mailchimp) should have instructions on how to do this or be able to help you.
- Fill out the DKIM request form.
- Wait for UTS to review and approve your request. This may take up to four business days and not all requests are guaranteed to be approved.
- If approved, you can start sending your bulk emails from your @mcmaster.ca email address. Make sure to follow the best practices for bulk email senders, such as providing easy unsubscribe options and keeping spam reports low.
This option will allow you to send your bulk emails without authenticating your account with UTS, but you will not be able to use your @mcmaster.ca email address as the ‘From’ address in the email. Instead, you will have to use an email address that matches the domain of your service provider, such as yourname@constantcontact.com. To do this, you will need to work directly with your email account or service provider.
