MFA Number Matching FAQs
No. Microsoft is mandating this change by default for ALL organizations. It is not configurable.
this can occur when you’re using your phone to login to a service and authenticate using the app. In this scenario, select “I can’t see the number” on the screen. This will hide the dialog for five seconds so you can see the number (example shown below).
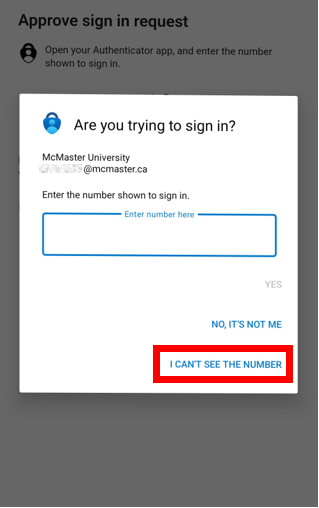
Older versions of Microsoft Authenticator may need to be upgraded to the latest version. Download the latest versions from the App Store and Google Play Store. The minimum version required for Android is 6.2006.4198, and the minimum version for iOS is 6.4.12. See here for more information.
Older versions of Microsoft Authenticator may appear different. Users need to upgrade to the latest version of Microsoft Authenticator for the best experience. Download the latest versions from the App Store and Google Play Store. The minimum version required for Android is 6.2006.4198, and the minimum version for iOS is 6.4.12. See here for more information.
If a user is running an older version of Microsoft Authenticator that does not support number matching, authentication won’t work if number matching is enabled. Users need to upgrade to the latest version of Microsoft Authenticator to use it for sign-in if they use Android versions prior to 6.2006.4198, or iOS versions prior to 6.4.12.
No, Apple Watch does not currently support number matching. You may need uninstall the Microsoft Authenticator Apple Watch app.
General MFA FAQs
MFA helps protect your account by adding an extra step to verify that you are who you say you are when you log on. In addition to your password, your account will be protected by “something you have,” such as a smart phone, mobile phone or a hardware token. This helps prevents hackers from gaining access to your account even if they know your password.
Hackers will always try to get our passwords, whether through phishing attacks, guessing attacks or by compromising other websites. MFA provides you the peace of mind that, even if your password is compromised, the hackers will not be able to access and use your account to further their attacks.
All members of the McMaster community, including faculty, staff, and students.
All McMaster students, faculty and staff are required to implement MFA on their Microsoft services/applications by April 2022. A rolling implementation will begin in January 2022, with information and support to be shared in advance and throughout the winter semester. However, there’s no need to wait! You can start today! McMaster students, faculty and staff can sign up for and use MFA right now.
There are several options to choose as your second factor:
- The Microsoft Authenticator smart phone app is the recommended method because of its ease of use and enhanced security. The app can be configured to use either a push notification (most convenient) or a verification code (most secure). The Microsoft Authenticator app includes additional benefits that you can leverage to protect your personal account. Click here for more information about the Microsoft Authenticator app.
- A hardware token is a small fob that provides you with a six-digit code that changes every minute and is used as your second factor.
How to request a hardware token. - SMS text messages can be used to send a 6-digit code to your mobile phone, then entering that code at log in as the second factor.
- Phone calls can be placed to your mobile or office phone to provide you a 6-digit code, then entering that code at log in as the second factor.
The Microsoft Authenticator App is the recommended method for second factor. You can download it by visiting the Microsoft Website here.
After you register for MFA, you will be asked to assert your second factor the first time you log on. You will not be asked to assert your second factor again when you log on from that device and in that location for at least 30 days (for employees) or 90 days (for students).
Only a few minutes. It is amazingly easy! Register here!
The Microsoft Authenticator app software token method does not require an internet connection and does not use cellular data. You can use it even your device is in airplane mode.
The Microsoft Authenticator mobile app is the recommended method for most users. It provides both online and offline code options to log in, which is useful if you are at an offline location. The Microsoft Authenticator app takes up very little space on your phone, and you can use the app without an internet connection or cellular data.
Not necessarily. Your password can still be compromised, and you will need to change it if that happens. We still recommend all the advice that we have always recommended with regards to secure passwords: use a unique and strong password that does not contain any dictionary words and a variety of character sets and continue to be on the lookout for phishing emails. If your password does not get compromised, you will not need to change it.
Password complexity requirement is different from multifactor authentication. You still need to change your MacID password when required if you suspect your MacID has been compromised.
When you log into your account and get prompted to use MFA
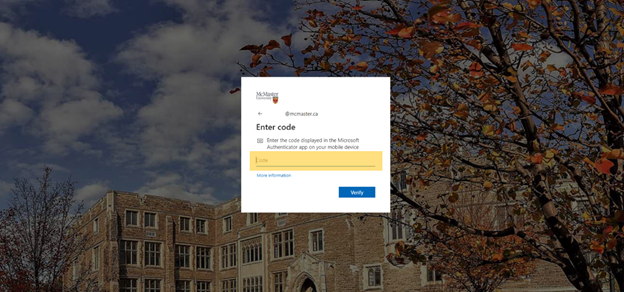
If you don’t have access to your app or have access to your app but don’t have access to Cellular/Wi-Fi and want to use a verification code click “I can’t use my Microsoft Authenticator app right now.”
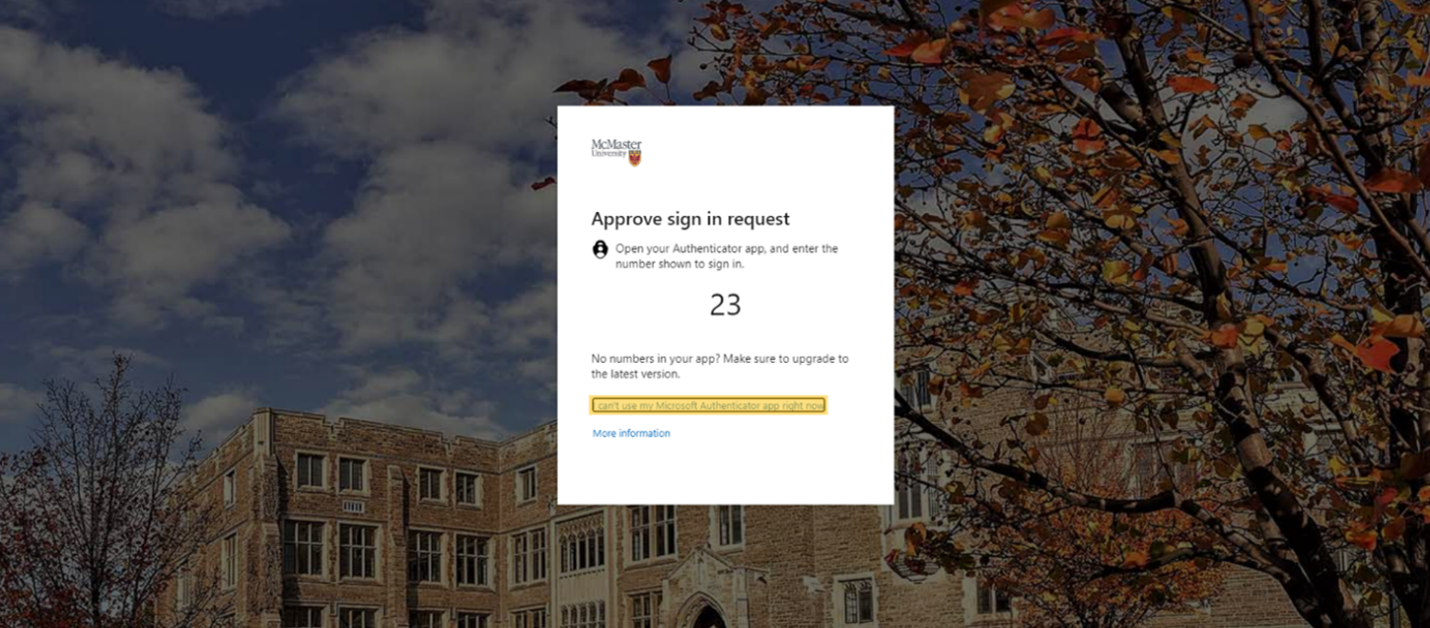
Then; “use a verification code.”
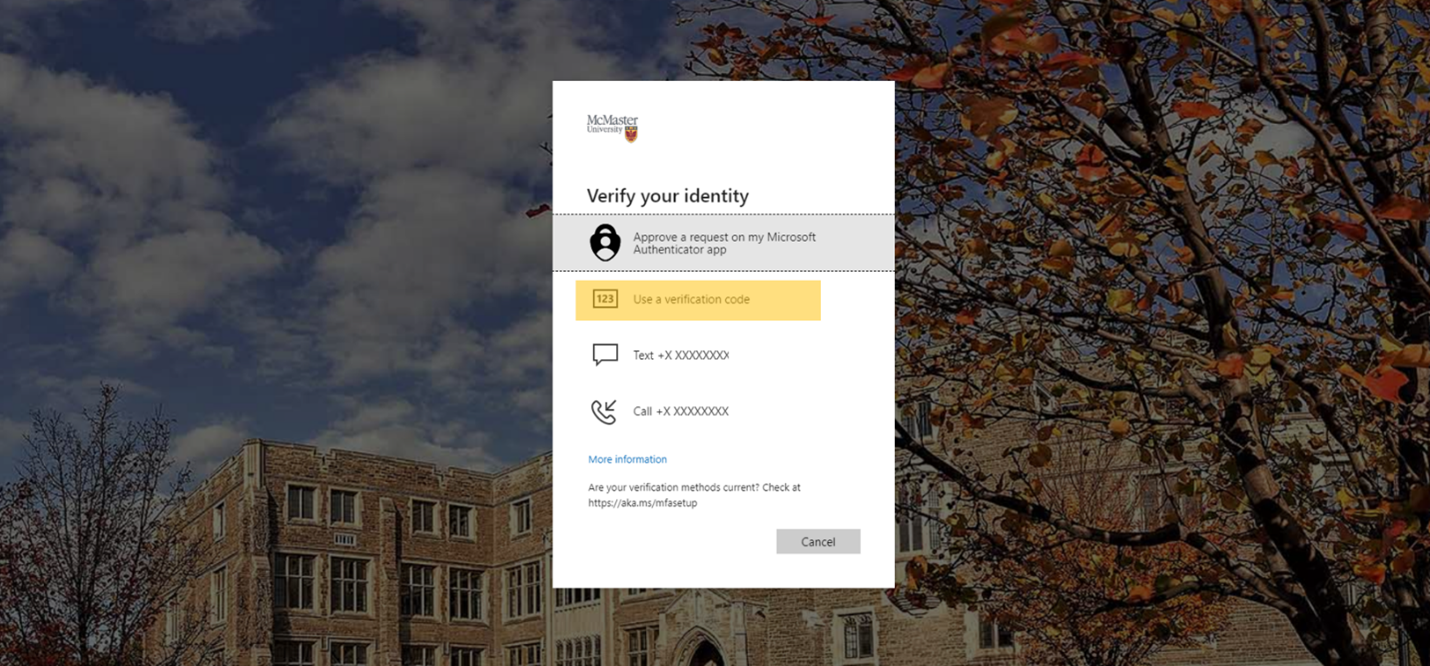
On your phone, Open your MFA app and click on your “McMaster University account”.
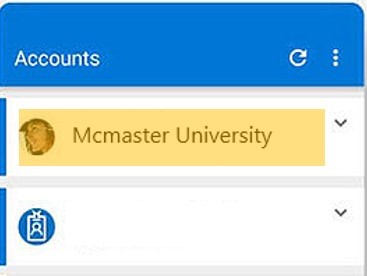
From there, you will see a “One-time password code” that will change every 30 seconds.
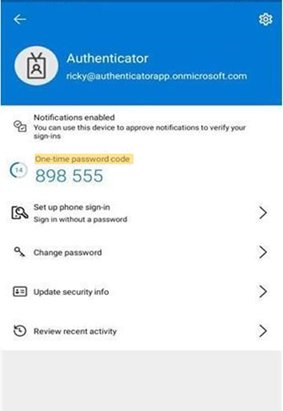
Type in the code in the text box and you should be logged into your account without the use of the internet.
Setup FAQs
When you register, you will be asked to setup multiple methods that can each be used to assert your second factor, then select one as the primary method. If you forget your primary at home, you can use one of the others that you configured. If that does not solve the problem, please contact the UTS Client Services for further assistance.
You can setup more than one device. We highly recommend that everyone add at least 2 devices.
The Microsoft Authenticator mobile app is the recommended method for most users. It provides both online and offline code options to log in, which is useful if you are at an offline location. The Microsoft Authenticator app takes up very little space on your phone, and you can use the app without an internet connection or cellular data.
Text messages and voice calls are sent only when you request them and would be billed by your carrier like any other text message or inbound voice call. The Microsoft Authenticator app push notification method uses very little cellular data and will use Wi-Fi if available. The Microsoft Authenticator app software token method does not require an internet connection, and as such, does not incur any expense.
The Microsoft Authenticator app software token method does not require an internet connection and does not use cellular data. You can use it even your device is in airplane mode.
The Microsoft Authenticator app software token method does not require an internet connection and does not use cellular data. You can use it even your device is in airplane mode.
When you received a push notification for a log on that you did not initiate, select DENY to prevent unauthorized access to your account. In these cases, your password may be compromised, and we recommend that you change your password immediately. Click here to go to the password management page.
No, the Microsoft Authenticator app is light weight and not intrusive. The app requires access to your camera to setup MFA using the software token method (i.e., to read the QR code), and does not access any other data on your phone. The app does not collect any information from your phone to send to McMaster or Microsoft.
Open the Microsoft Authenticator app and click on Settings. Use Logs to control what data is sent to Microsoft.
Retirees/Professor Emeriti FAQs
Yes, all former Professors and Professors Emeriti will be required to use MFA.
No, it is not a requirement that you use MFA to login. You have the option to signup voluntarily if you feel if provides you the best security protection for your account.
Concerns
Yes, other universities and colleges are using MFA to better protect their data and accounts.
Select “work or school account”.
No, you enroll only once when you sign up for MFA.
No. MFA does not cause any slowdown to the performance of your applications.
Yes, you can change/update or add more verification methods at any time by visiting your security information.
No, after asserting your second factor, your computer will be trusted from that location and device for 30 days (for staff) or 90 days (for students). You will not be prompted to assert your second factor again unless you switch locations or log on from a different device.
When you received a push notification for a log on that you did not initiate, select DENY to prevent unauthorized access to your account. In these cases, your password may be compromised, and we recommend that you change your password immediately. Click here to go to the password management page.
Travel FAQs
- Ensure if you have a Canadian and international phone number you add both to your account so you can access it outside the country https://aka.ms/MySecurityInfo
- Signing up with the Microsoft Authenticator App will allow you to login from Canada and internationally without a cellphone service, or Wi-Fi https://office365.mcmaster.ca/mfa/#tab-content-microsoft-authenticator-app
- If you know you will be traveling, you can change your default sign-in method here https://aka.ms/MySecurityInfo as well as add different methods of verification to your account
- If you do not have a smartphone and need to access your account, please put in a hardware token request form in advance so you are able to have the token with you during travel https://office365.mcmaster.ca/mfa/#tab-content-getting-started (located near the bottom of the screen)
Yes, you can change/update or add more verification methods at any time by visiting your security information.
The Microsoft authenticator app as it is light weight and non-intrusive to the phone as well as does not require data or cell service. If you do not have a device we recommend the hardware token.
Change/update your default-sign-in method by visiting your security information.
Yes you can use the MFA app internationally at any time free of charge.
